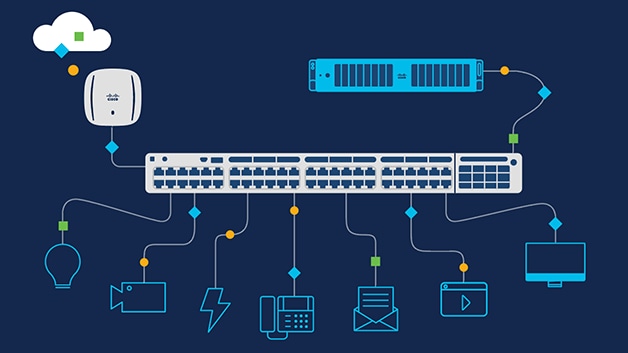
Switches connect users, applications, and equipment across a network. They also reduce data collision in high-traffic areas and help protect networks from cyberattacks. The most straightforward switches offer connectivity exclusively to devices on a single local area network (LAN). More advanced switches can connect devices from multiple LANs and may incorporate essential data security functions.
Security
Switching in networking security is crucial to a company’s IT infrastructure, protecting sensitive data, applications, and other information from cyber threats. It also ensures that the network continues functioning and is usable for users. Many organizations use network security tools and technologies to protect a network from security breaches. These include hardware and software solutions. For example, a firewall prevents hackers from entering an organization’s network. However, the threat environment is constantly changing, with attackers trying to find new vulnerabilities to exploit. As a result, a network security management system is needed to update security policies and enforce them across the network. The management system can create security rules for various devices, including firewalls, VPNs, protocols, and NAT. A network switch also has a MAC address table, which stores the MAC addresses of all the devices connected to it. When a packet arrives on one of the switch ports, it looks for a MAC address in its table to determine where to send the data. If the MAC address isn’t on its list, it sends the data to another port.
Port Mirroring
Port mirroring is a technique that forwards a copy of each packet received or sent on a specific port to another port. The method enables administrators to monitor network performance and analyze traffic with the help of protocol analyzers attached to the second port without affecting the packet processing capabilities of the first port. The technique is commonly used for network appliances requiring monitoring of network traffic, such as intrusion detection systems (IDS), passive probes, or accurate user monitoring (RUM) technology that supports application performance monitoring (APM). It also helps administrators keep a close eye on their network and alerts them when problems arise. To enable port mirroring, configure the switch to send a copy of network traffic on a specified port or VLAN to a network monitoring connection on a different switch port. The switch forwards the mirrored packets to devices running an analyzer application. A device attached to a mirror output interface can use an analyzer application to perform tasks such as monitoring compliance, enforcing policies, detecting intrusions, monitoring network performance, correlating events, and other problems on the network. The device can also analyze mirrored traffic to identify the source of a network bottleneck or determine where to improve performance. If many ports are used for mirroring, the internal forwarding bandwidth on the switch may be affected because of the heavy load. This can result in the observing port failing to forward the mirrored packets on time, leading to packet loss. It is, therefore, essential to limit the amount of mirrored traffic and to choose only the interfaces that require the analysis.
Routing
Routing is choosing the best path for data packets to take between networks. This is essential for a network to function and is performed within routers. A router uses its routing table – lists of IP prefixes – to decide which route data packets should take when they reach another router. It also shares its routing table with other routers through different routing protocols so that they can all make informed decisions. In many large networks, routing is a complex and essential part of network security. Whether it’s power grids, phone networks, or the Internet Protocol (IP) network, routing is crucial to ensure that data traffic is sent efficiently and without disruption. While the network administrator sets static routing tables and only changes them if manually updated, dynamic routing tables can proactively predict the shortest and fastest routes for sending data packets. They do this by analyzing network conditions and adjusting their routing algorithms accordingly. Dynamic routing protocols, such as RIPv1 and OSPF, automatically adjust their routing algorithms in response to changes in topology or condition. This helps ensure that routers use the shortest and fastest routes possible while avoiding disconnected networks or high-traffic routers. The routing algorithms are designed to use various metrics, such as hop count, bandwidth, and delay, to determine the shortest, most efficient path for data packets. Generally, lower metrics indicate a better approach.
Management
Network management is a critical component of network security. It covers everything from adding and inventorying network resources to setting up operating systems, software updates, and management tools. Management is essential to network security because it enables your organization to plan and implement changes effectively. These changes include increased bandwidth connections, updated network operating system software, and security patches to protect your business from threats. One of the most important aspects of network management is managing switches, which are critical for the security of your LAN. Switches allow your network to distribute traffic between connected devices and improve overall performance. A network switch can offload traffic in more extensive networks and facilitate intrusion detection, performance analysis, and firewalling. A switch can often mirror data before sending it to an external device. Another important aspect of switching is that it provides intelligent network routing. This means that it can advance frames based on the origin MAC address of the packet, which increases overall network efficiency. Intelligent switching allows your network to handle increased traffic and bandwidth requirements. This includes video and other bandwidth-intensive applications, more user devices, and more packets destined for servers and cloud storage.